|
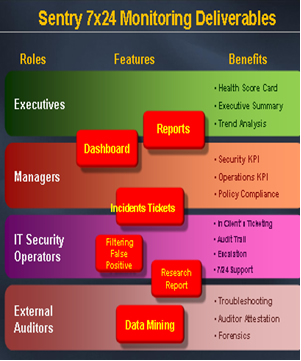
ERE's service for monitoring network security and compliance is by far the most comprehensive, granularly tunable, and effective service available to any enterprise. Through continuous monitoring of network devices and critical assets, events are collected, filtered, correlated against time and against all other monitored devices. False positives are eliminated in real time. We evaluate hundreds of thousands of monthly security log events and other log analyzer events for each client and reduce them to handfuls of clear, actionable trouble tickets.
ERE 24x7 IT security auditing service keeps an electronic eye on event log management data, security and operational alerts / alarms and manually provided attestation documents in order to identify compliance violations against corporate policy, privacy policy, SOX, CSOX, NERC CIP, ITIL, COBIT, ISO, etc. Our service brings computer security monitoring into a new paradigm of usefulness and ease of use for clients who need security information and event management.

Differentiators – 7/24 IT Security Monitoring and 7/24 IT Security Auditing Service
-
No agents to be installed on a client's network. Our 7 24 IT security monitoring service which includes our 7 24 IT security auditing service has agents only on one data collector device for which the client has complete control.
-
100% passive service. Our 7/24 IT security auditing service has no ability whatsoever to affect a client's network.
-
Granular custom reporting and tuning that client IT operations team requests, ongoing.
- Respond to client questions / requests 7/24.
- Analyze complexities to identify meaningful incidents prior to sending our trouble tickets.
- Focus on correlations that clients want but can’t get, for example:
- Active directory : stale accounts : HR changes.
- Software monitoring log events : failed accesses
- Active directory : WSUS: patching system.
- We launch MBSA : active directory : corporate policy control points.
-
Control points : attestations / signatures : timeframe thresholds
- Firewall log events : IDS tap inside network : IDS tap outside network
- Suspicious activity from outside the network : IP addresses : period of time
- Failed access attempts : domain : timeframe : SOX control point
- Any other collection of fields a client requests we correlate and alert / report.
24x7 Managed Security Service
For our clients who do not wish to manage their own network IDS and HIDS, we provide for those technologies 24x7 Managed Security Service.

Contact us right up front
Network security monitoring and monitoring security logs should deliver clear, actionable reports; not huge amounts of analysis. Let ERE do all the back end analysis, triage, first level testing and get the job done. Contact us now save you time cost effectively with our 24x7 IT security monitoring and 24x7 IT security auditing services.
|

